I’m in the end-stages of finishing off my centralized Let’s Encrypt solution and I’ve released my code as an open source project named anvil. I’ve also created a FreeBSD port.
In this post, I outline the anvil tools and how I use them. In future posts, I will detail the individual components, some of which have already appeared in my blog.
Why centralized
After reading about the FreeBSD cluster’s use of Let’s Encrypt, I immediately took to the concept of a centralized certificate process. Should there be an exploit in the acme protocol, you have only one location to deal with. I also did not want to deploy a Let’s Encrypt client to every server which used an SSL certificate. Instead, I wanted one location which dealt with certificates, and then I would create a certificate distribution system. Certificate keys would be distributed out of band.
In addition, I wanted to use certificates for more than just websites (e.g. smtp, imap). Authorizing those certificates via http would be non-trivial, which means dns authorization is the preferred option. For security reasons, I would rather have the DNS updates occur only in one location.
All of the above leads to a centralized solution.
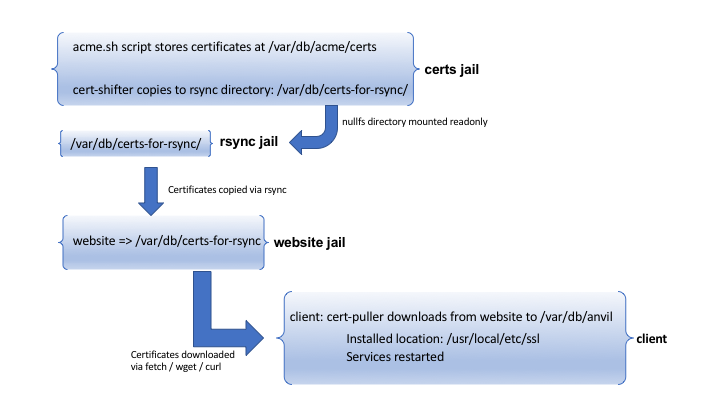
My configuration consists of three main parts:
- A FreeBSD jail to obtain certificates via the acme.sh client
- A website to provide the distribution path for the certificates.
- A script to download the certificate, install it, and restart services as required.
All tasks are carried out via non-privileged users, with the occasional use of sudo where absolutely required. The installation makes use of read-only data as much as possible to reduce the threat-vector at each stage.
anvil
anvil is for distribution only. It is not used for certificate creation. For that, you would need a Let’s Encrypt client. I use acme.sh.
The tools provided by anvil include:
- cert-shifter – copies certificates from your source directory (i.e. where acme.sh created them) to another directory. Keys are not copied. I call this location the rsync directory. We avoid leaking the keys by moving the certificates to another directory
- cert-puller – pulls certificates down from a website, installs them, and restarts services (e.g. apache, dovecot, postfix).
There is a step between cert-shifter and cert-puller which is not mentioned above. I call that the rsync step.
This diagram helps to explain the process:
Works with multiple certificates & services
anvil can work with just one certificate and one service, or as many as you want. Flexibility is by design.
My next task is to document each stage of the above in a series of blog posts. Collectively, they will show you how to get started with a centralized Let’s Encrypt solution.











